[SWPUCTF 2022 新生赛]Capture!
Problem: [SWPUCTF 2022 新生赛]Capture!
[[toc]]
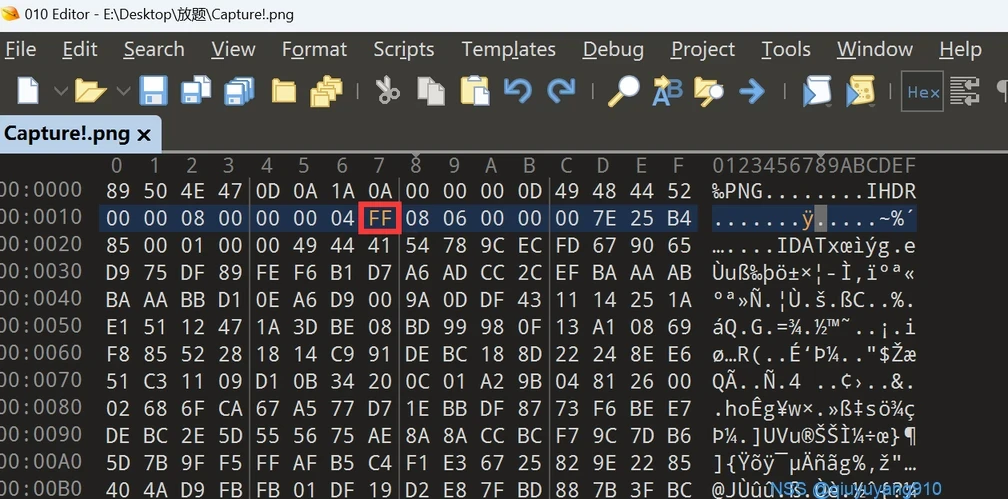
修改高度得part1
再LSB隐写一把梭
zsteg -a flag.png #一把梭
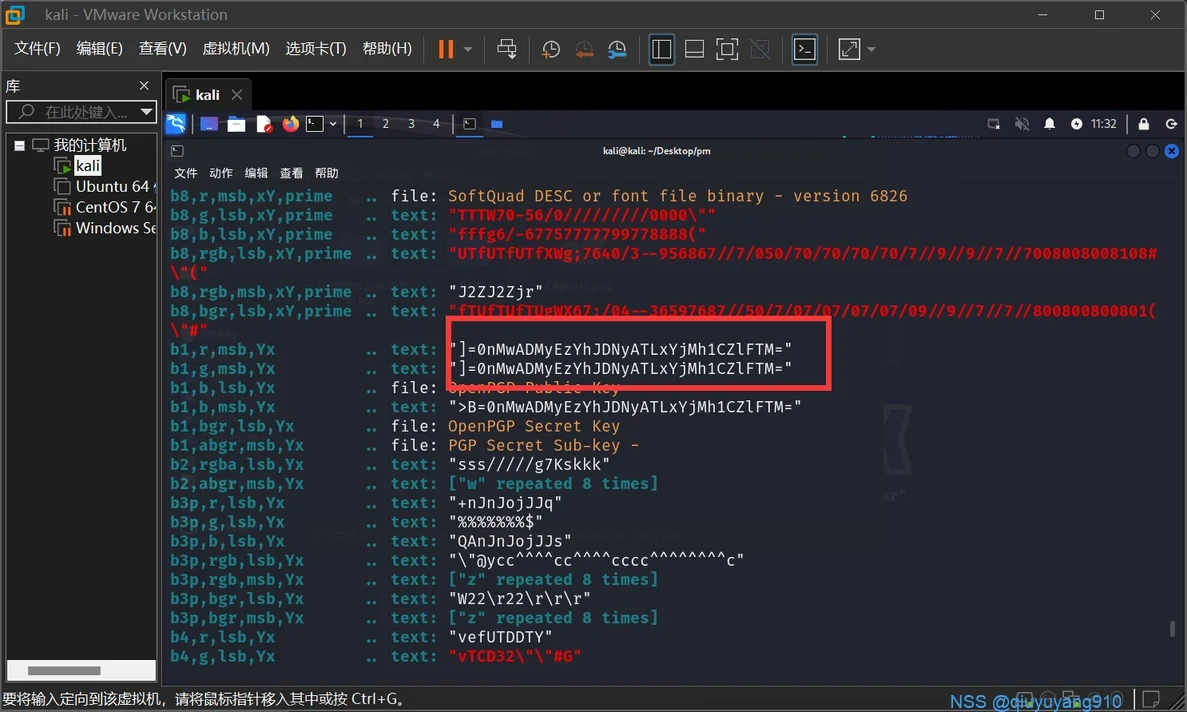
猜测base64,无果
再颠倒顺序即可解出
[SWPUCTF 2022 新生赛]Cycle Again
Problem: [SWPUCTF 2022 新生赛]Cycle Again
先用010查看图片发现图片的宽和高为零即可知是crc爆破
再用脚本crc爆破
import binascii
import struct
# \x49\x48\x44\x52\x00\x00\x01\x00\x00\x00\x00\x00\x08\x02\x00\x00\x00
crc32key = 0x6bb7ad9c
for i in range(0, 65535):
for j in range(0, 5000):
width = struct.pack('>i', j)
height = struct.pack('>i', i)
data = b'\x49\x48\x44\x52' + width + height + b'\x08\x06\x00\x00\x00'
crc32result = binascii.crc32(data) & 0xffffffff
if crc32result == crc32key:
print(''.join(map(lambda c: "%02X" % c, width)))
print(''.join(map(lambda c: "%02X" % c, height)))
output:
00000800
00000480
即可得到part1
再用crc爆破压缩包即可获得part2
[SWPUCTF 2022 新生赛]Coffee Please
解压文档
使用vscode 搜索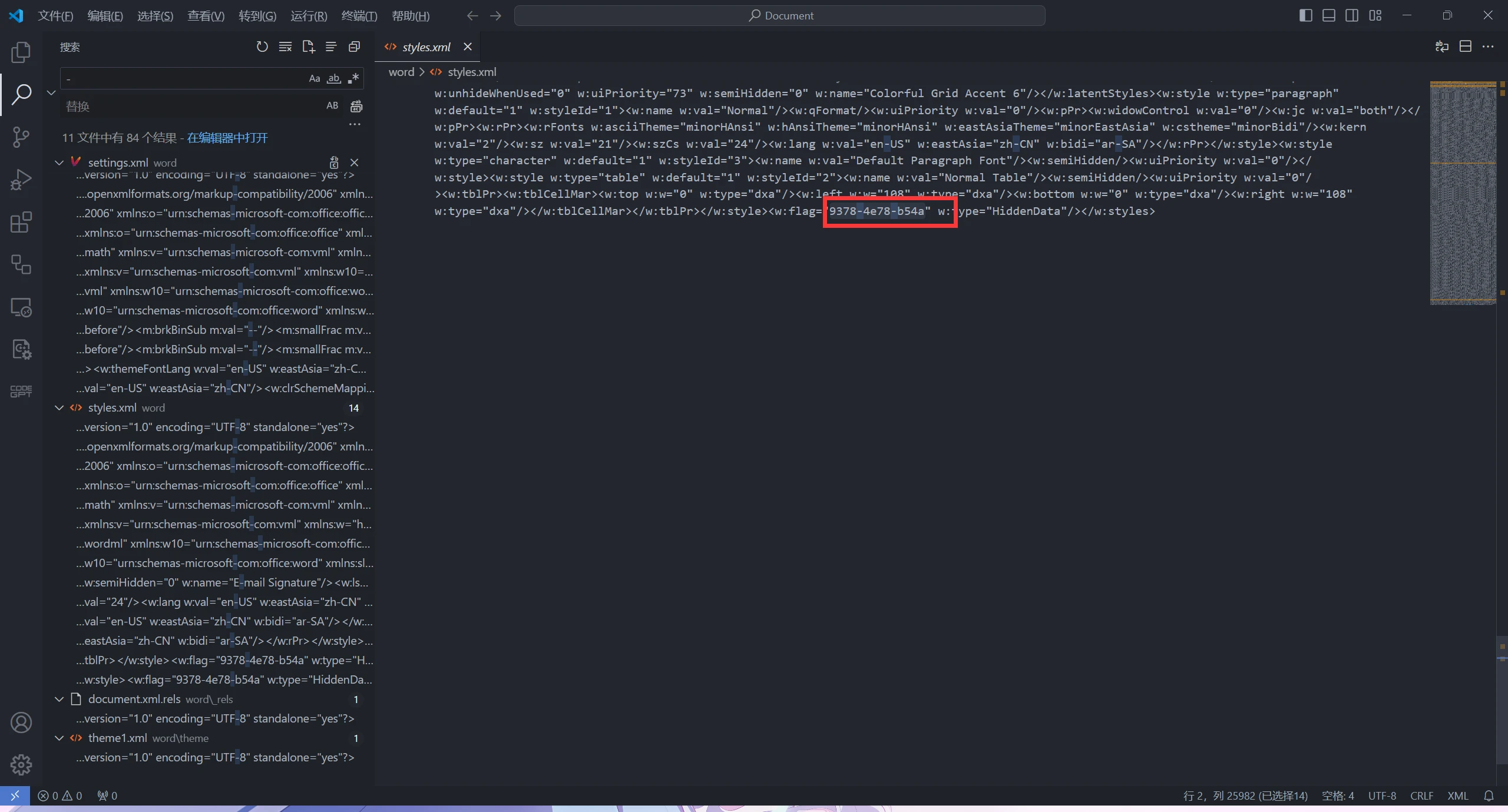
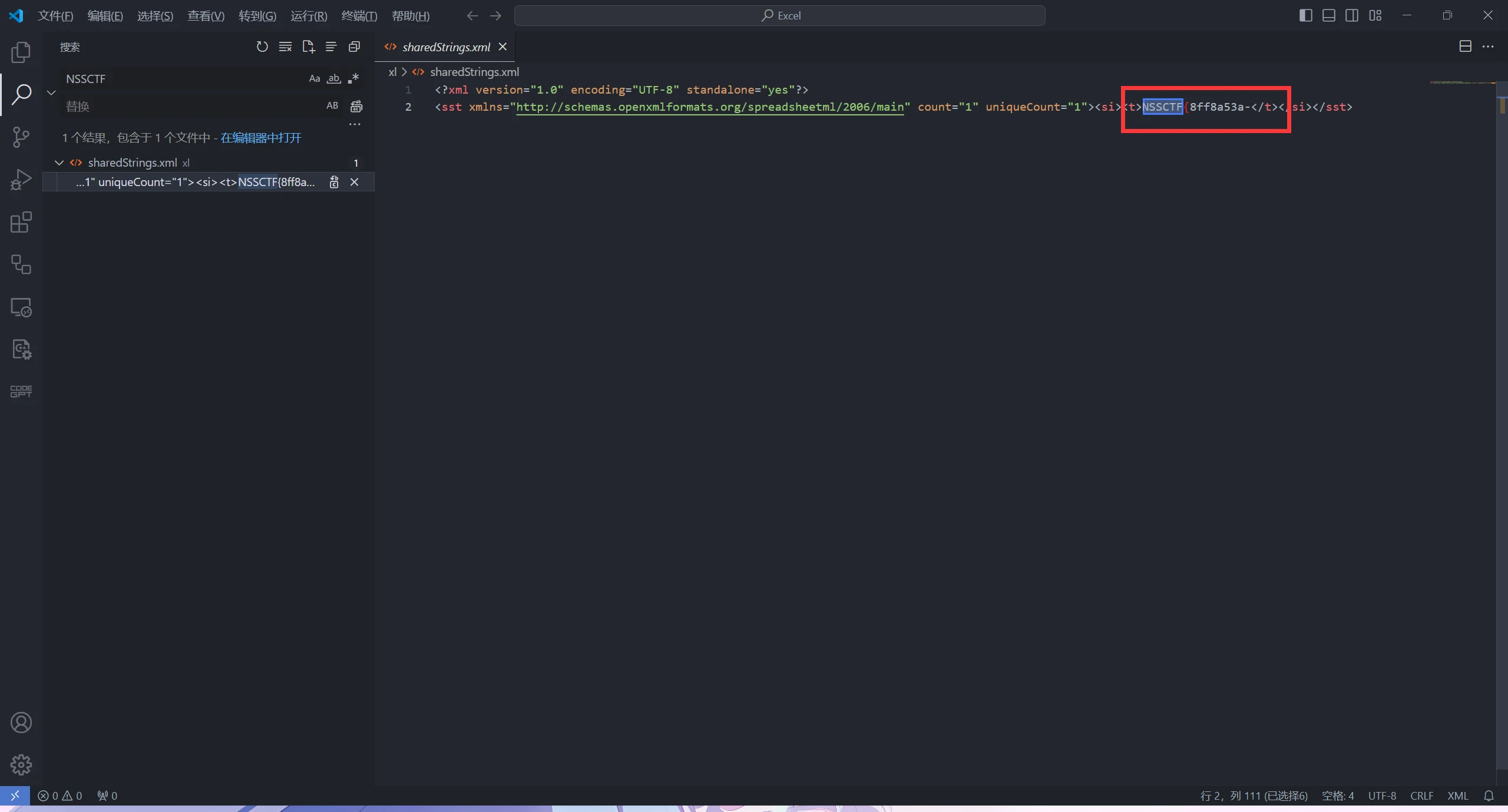
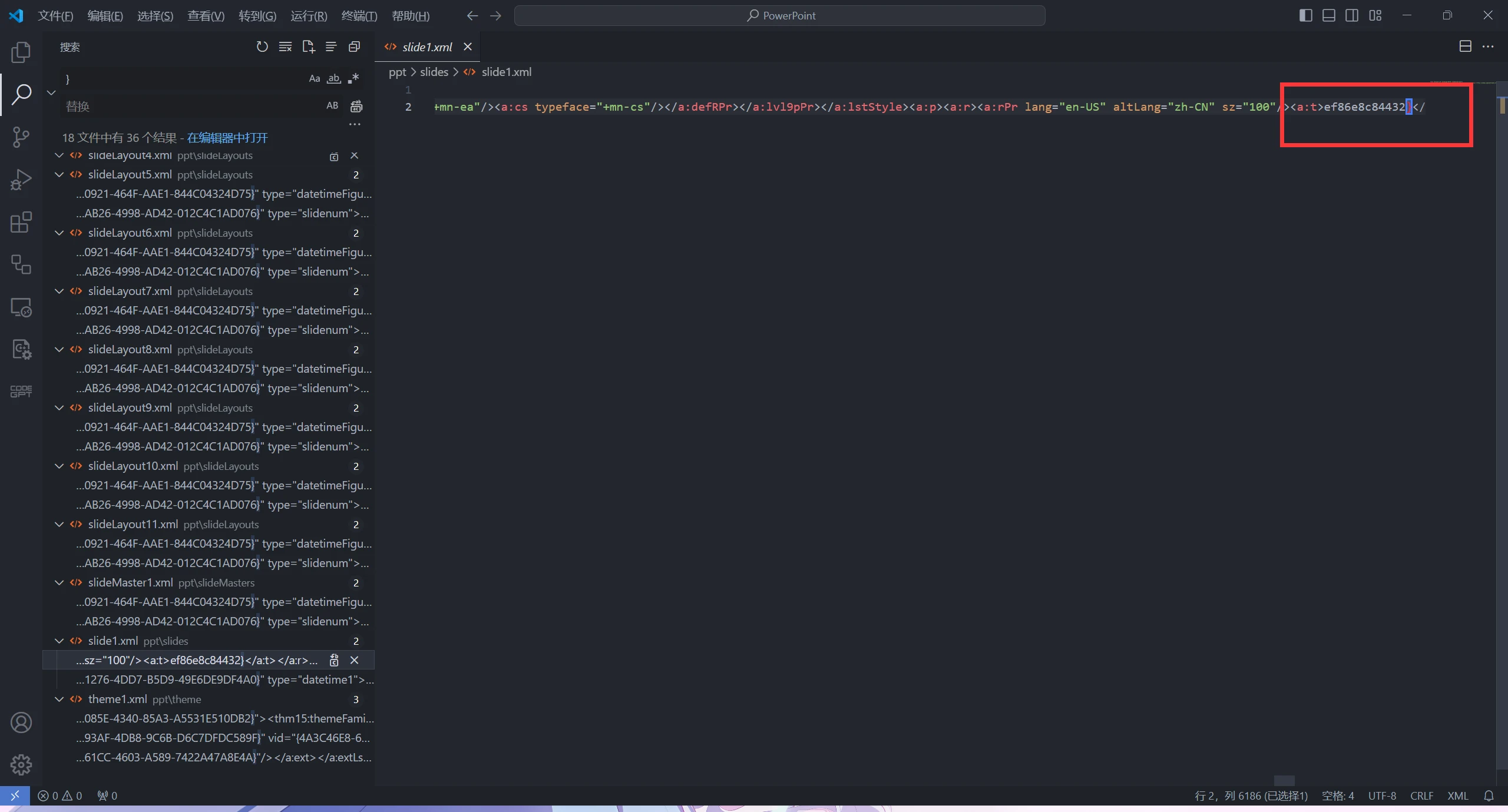
即可得到flag
NSSCTF{8ff8a53a-9378-4e78-b54a-ef86e8c84432}
Problem: [SWPUCTF 2022 新生赛]Convert Something
[SWPUCTF 2022 新生赛]Convert Something
零宽隐写+base64隐写
零宽隐写
网站
base64隐写脚本
import base64
def get_base64_diff_value(s1, s2):
base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
res = 0
for i in range(len(s1)):
if s1[i] != s2[i]:
return abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))
return res
def solve_stego():
with open('.\字频统计.txt', 'rb') as f:
file_lines = f.readlines()
bin_str=''
for line in file_lines:
steg_line = line.decode().replace('\r\n', '')
norm_line = base64.b64encode((base64.b64decode(line))).decode()
diff = get_base64_diff_value(steg_line, norm_line)
pads_num = steg_line.count('=')
if diff:
bin_str += bin(diff)[2:].zfill(pads_num * 2)
else:
bin_str += '0' * pads_num * 2
print (bin_str)
res_str = ''
for i in range(0, len(bin_str), 8):
res_str += chr(int(bin_str[i:i+8], 2))
print (res_str)
if __name__=='__main__':
solve_stego()
```
# [SWPUCTF 2022 新生赛]Does your nc work?
>https://www.nssctf.cn/problem/2633
nc 连接签到题,注意不要用windows连接就行
# [SWPUCTF 2022 新生赛]funny_web
> Problem: [[SWPUCTF 2022 新生赛]funny_web](https://www.nssctf.cn/problem/2637)
账号NSS
密码2122693401
intval()函数用于字符串转整数,可以使十六进制转十进制用于绕过数字过滤
intval()函数绕过,可以凭借字符串拼接绕过
payload:?num=12345a